
In March 2000, an Irish grad student named Ian Clarke created the software application, Freenet. This was the initial framework for anonymous communication and file sharing. Later in 2022, the US Naval Research Laboratory built on Freenet’s idea to create a secure and encrypted network for sensitive communications, which was later released to the public as open-source software. If you’re using a browser like Tor and visiting .onion websites that aren’t accessible through regular search engines or browsers, you’re likely on the dark web.

Users are able to authenticate themselves and they have the option to enable 2FA. It also has a message option to communicate with vendors or customers, users’ orders are tracked and there is a forum linked to this market. Onion sites aren’t really dangerous, but they could be when accessed through unfamiliar or suspicious links. The website has an advanced search filter and an easy-to-use interface, which makes it easy to find what someone is looking for.
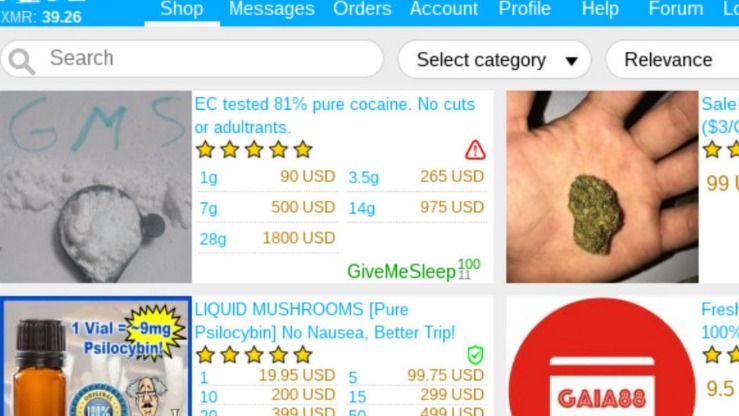
Onion Links: How To Access Them
These actions were part of a coordinated effort among US government agencies and foreign counterparts to combat Russian illicit finance. While Mega’s inflows declined by more than 50% year-over-year (YoY), Kraken DNM’s rose nearly 68% YoY. Kraken DNM, which billed itself as Hydra’s Market’s successor, received $737 million on-chain in 2024. Blacksprut, which rose to prominence with Mega in the wake of Hydra’s 2022 sanctions designation, law enforcement seizure, and subsequent collapse, came in third with 13.6% less revenue YoY. “The Trade in Small Arms and Light Weapons on the Dark Web” can be accessed online here.
Did The Silk Road Marketplace Go Under?
Cybercriminals go on dark web marketplaces to buy and sell illicit goods and services. They engage in financial crime and sell other people’s stolen personal information, since they’re under the veil of anonymity. Many people go to the dark web to buy things they can’t find elsewhere, but what if what you’re buying is also trying to harm you?
As mentioned earlier, launching a cyberattack doesn’t require any hacking skills. Even people with zero technical knowledge can buy phishing kits, ransomware, or stolen logins. Imagine trusting a site where you’ve been buying or selling for months, and everything seems legit. Some marketplace operators first build trust by running a legitimate platform. Some sellers offer cracked versions of expensive software that you’d typically pay hundreds of dollars for.
Table Of Contents
In Colombia, for instance, many of the vendor listings are for cocaine or Infrastructure-as-a-Service, as seen in the screenshot below. The Camouflage Mode is intended for people living in countries with heavy internet censorship, like China. It will make your VPN activities seem like normal traffic, so you can use an uncensored internet. However, this feature is only available on iOS, Android, and Windows. The VPN will protect your traffic when you connect with military-grade AES 256-bit encryption.
How To Access onion Sites Safely
Others sell pirated eBooks, academic materials, and entire premium courses ripped straight from paid platforms. Unfortunately, the dark web hosts not only explicit but also deeply illegal and disturbing content. The markets often share materials related to child exploitation, pornography, and non-consensual recordings, all of which are serious crimes that inflict lasting harm on real-life victims. Such content fuels a dangerous cycle of abuse, violence, and exploitation. It brings in vendor reviews from other places and verifies them using PGP signatures, so buyers can feel a bit more confident about who they’re dealing with.
It relies on P2P connections and requires specialized tools and software. Tor and I2P are the two commonly used tools for accessing the dark web to provide anonymity. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa. The dark web isn’t just one sketchy marketplace hiding in a corner of the internet; it’s more like a messy, unregulated community with everything from freedom fighters to full-blown cybercriminals.
Exploring The Onion Dark Web: A Comprehensive Guide
If the operating system detects any non-anonymous connection, it blocks it, thus ensuring maximum online protection. They use pseudonymous wallets, privacy coins (like Monero), mixers, chain-hopping, and non-KYC platforms to obscure transaction trails. One of the most common is the exit scam, where a marketplace suddenly disappears and takes everyone’s money with it. Ransomware and cryptocurrency-based crimes saw a significant increase in 2023, with a nearly $176 million rise compared to 2022. Remember, staying informed is your best defense against misinformation.
A Quick Guide On How To Use A VPN With Tor
In April 2016, its APIs were compromised, resulting in stolen messages. But since its relaunch, the developers are focusing more on operational security and ensuring that users can have a good experience on this site. The Abacus Market links to the new dark web marketplace sections and took over much of the vacuum left by the AlphaBay takedown. It’s been a constant back-and-forth between cybercriminals and law enforcement, with each new site trying to be smarter and more secure than the last.
- In due course, the framework was remodeled and made public as a secure browser.
- It helps us stay more vigilant, better protect ourselves, and make informed decisions online.
- Our mission is to simplify navigation in the complex and evolving world of the darknet.
- The website has a sleek design and interactive user interface, making it the most preferred choice in terms of user experience.
- If you’re into a darknet market that feels cutting-edge and keeps your coins safe, ASAP Darknet Market’s a gem—just don’t expect a massive catalog yet; it’s more about precision than sprawl.
A network browser gives you access to sites with the ‘.onion’ registry operator. Cryptocurrencies such as Bitcoin have been the dark web currency even before they became available to the general public. Right now, you can use many cryptocurrency .onion sites to buy or sell all types of cryptocurrencies.
Furthermore, data will help to detect attacks against the network and possible censorship events. In some countries, such as China and North Korea, the government uses heavy online censorship and blocks many dark web websites. This is where an Onion website, like the Tor browser, comes in handy. The social media giant is also aware of the many attempts by repressive regimes to restrict its access. After all, it enables users to connect and communicate with each other from around the world. You can choose the best darknet (.onion) website that suits you and start surfing.

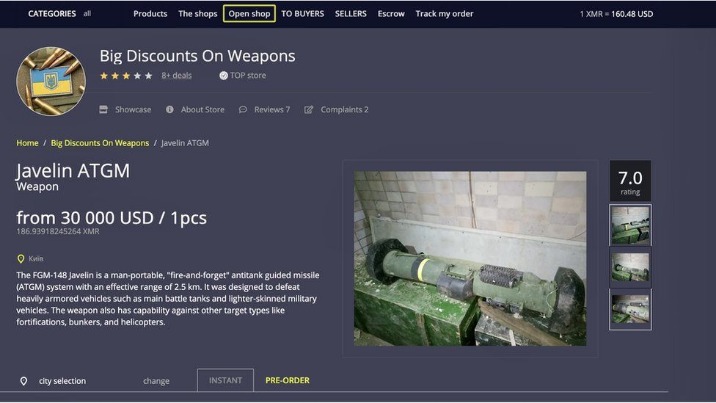
We may earn a commission when you buy through links on our sites.©2025 GIZMODO USA LLC. The overall value of the arms listings examined by Rand was estimated at roughly $80,000, of which handgun made up 90 percent. Further market diversification occurred in 2015, as did further developments around escrow and decentralization. This material is for informational purposes only, and is not intended to provide legal, tax, financial, or investment advice. Recipients should consult their own advisors before making these types of decisions. Chainalysis has no responsibility or liability for any decision made or any other acts or omissions in connection with the use of this material.
For example, tracking cryptocurrency transactions can provide insights into certain groups involved in the trade. It is crucial, however, that law enforcement agencies keep pace with evolving technologies and methodologies employed by dark web vendors to maintain efficacy in combating these illicit markets. The dark web is characterized by anonymity and privacy, allowing users to conduct their activities without fear of surveillance. This intrinsic quality has attracted various communities, from political dissidents seeking refuge in oppressive regimes to individuals engaging in illegal activities, including the trade-in weapons. At the surface, users access the “clear web” via standard search engines, which indexes readily available and legal websites. Beneath this lies the “deep web,” which consists of databases and other resources not indexed by standard search engines.



