You can also find email messages, online bank statements, and much more information on the deep web – information that is usually private and inaccessible by the public on the surface web. The majority of the web is called the “deep web” (often referred to as the “invisible” or “hidden” web). The deep web is basically all the content that you can’t find using Google or Yahoo search. So, sites that contain a domain extension like .com, .org, .net, .biz, .info, etc. can be found on the surface web. In addition, the content on the pages don’t need any special or custom configuration to access. Did you know that Google only shows you a glimpse of all the websites that actually exist?
Getting Started: Accessing The Dark Web Safely

Malicious actors often target browser plugins to steal website credentials or install malware on unsuspecting devices, so Tor sidesteps these risks altogether. However, the most secure way to use Tor is via .onion sites, which are built exclusively for the Tor network. The Tor browser routes your online requests through multiple nodes to obscure them from prying eyes. It conceals your location and other personal data that are exposed when using standard browsers.
- We’ll use the Tor browser for this guide, but any other browser that supports the Tor protocol will do.
- So, you’ll be happy to know there are several easy ways to delete a page in Word, including both blank pages and those you simply no longer need.
- Malicious actors and government agencies can run Tor nodes, compromising privacy and security.
- For a limited time, new users who purchase any plan can claim 25% off their first order.
- While an iOS version of the official Tor browser is not available, there are Tor-compatible browsers available in the App Store.
- Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution.
In 2002, the dark web grew significantly when researchers supported by the US Naval Research Laboratory built and released the Tor network. At the time, the internet was still young, and tracking people was easy while staying anonymous was not. The Tor network allowed safe communication channels for political dissidents and American intelligence operatives around the world. Regular dark web visitors know that it’s possible to exploit the sketchy reputation of the space and the services offered. And though some dark web marketplaces offer user reviews, not all do.
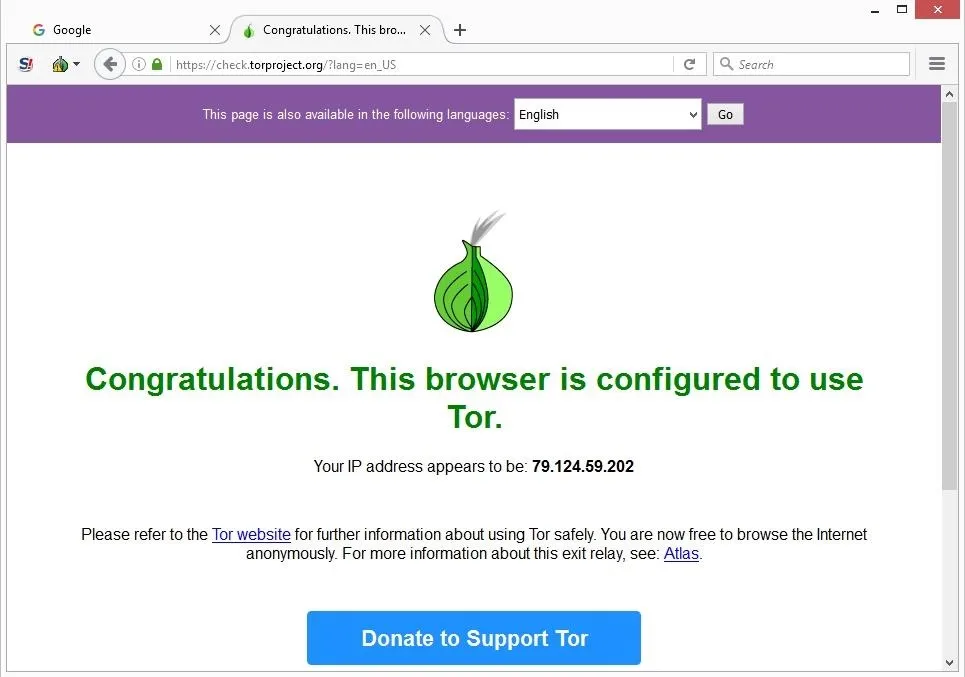
Install The Tor Browser
Antivirus will ensure that any viruses or malware downloaded from the dark web are removed. Accessing the Dark Web safely in 2025 demands vigilance, preparation, and strict adherence to security best practices. By carefully following the safety procedures outlined in this guide, you minimize your risk of encountering malware, fraud, or legal troubles. Always remember, your safety online depends significantly on personal responsibility, informed decisions, and proactive application of security tips. Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape. Lokinet is easier to set up than I2P, and it may run faster than Tor in some cases, especially when visiting regular websites through its secure network.

WANT TO TRY THE TOP VPN RISK FREE?
Despite the presence of illegal marketplaces and the trading of sensitive information, the dark web also offers a place for anonymous communication, social networks, and lawful content. In addition, know that while accessing the dark web is legal in most countries, engaging in illegal activities (buying or selling contraband, hacking services, etc.), is illegal everywhere. You should be aware that law enforcement agencies may be monitoring the dark web and that visiting certain websites or engaging in illegal activities can result in criminal charges. You can also check out this ultimate dark web safety guide to browse safely.
Step-by-Step Guide
However, there is an easy-to-use way around that, which we’ll talk about later. Once the file is downloaded, run it to launch the installer and follow the prompt until the Tor browser is installed. Upon selecting the button for your operating system, you will be prompted to download the installer, which you should save to a folder. Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android. We already went through VPNs, anonymizing web browsers, and disposable operating systems, so I won’t bother reminding you about those. Fortunately, in Hidden Wiki, every website is followed by a brief description so that the user knows what to expect.
Don’t Reveal Any Personal Information
However, the first Tor server you connect to can see your real IP address — if a malicious actor operates it, they could collect it and use it to track your location or online behavior. I strongly recommend avoiding unofficial sources, as you risk downloading malicious software. When it comes to accessing the dark web (and safely), selecting a good dark web browser is critical. Tor Browser is the #1 in our list above for all the good reasons. We recommend that you use only the Tor browser to access the deep, dark web, if you must.
For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that. By using Tor and a reputable VPN, along with being careful and having the right tools, you can browse the dark web legally and safely. Responsible use protects your privacy while staying within the law, so it’s a safe place to browse for real privacy reasons. Navigating the Dark Web can be a complex endeavor, but you don’t have to do it alone.

Stolen Data And Identity Theft
The beginning of the dark web is generally seen as coinciding with the release of Freenet in 2000. As the thesis project of Ian Clarke, a student at the University of Edinburgh in Scotland, the Freenet was built to help people anonymously communicate, exchange files, and interact online. Additionally, check the Block pop-up windows and Warn when websites try to install add-ons settings. So, you should never share your personal information on the dark web.
Is It Safe To Log Into Accounts While Using A VPN And Tor?
Some of these sites can be found through regular web browsers, but you’ll then need to switch over to Tor once you’ve got the onion links you want to follow. It’s a part of the internet that’s less regulated and more shadowy, for better and for worse. I2P is an anonymous overlay network that can only be used to access hidden websites and services that are unique to the I2P network. You cannot use I2P to access .onion sites because it is a separate network from Tor. So much, in fact, that you can’t use this method for downloading anything, or even for watching videos.
They change your browser fingerprint and make you easier to track. Setting up Tor correctly is critical if you want to browse the dark web without exposing your real identity. A single misstep, like skipping a leak test or using the wrong browser, can undo all your privacy efforts. Keeping your VPN and Tor Browser updated ensures you benefit from the latest security patches. Outdated software can have vulnerabilities that may put you at risk.
This guide reviews tools such as Tor, I2P, Whonix, and more for accessing the hidden web securely. Onion.pet is another similar service that works slightly better than Tor2Web. Just replace the “.onion” suffix with “.onion.pet,” and you should be able to access onion sites in your browser. These communities, which include private social media platforms, allow like-minded individuals to connect, collaborate, and share information freely and anonymously.
However, because it’s almost completely anonymous, there are a lot of illegal images, information, products, and services on the dark web. Attempting to even view these can be illegal in many countries and states, so stay well clear of them if you want to keep a clean record and conscience. As the most widely used anonymity network, Tor routes your internet traffic through a series of volunteer-run servers (relays) around the world. This “onion” routing masks your IP address and encrypts your data multiple times, peeling away layers of encryption at each relay. With rising curiosity around hidden corners of the internet, many professionals wonder, “how to access the dark web” safely. From cybersecurity researchers to IT managers, understanding how to navigate the dark web can help monitor cyber threats, protect sensitive data, and investigate cybersecurity incidents.
Examples include password-protected websites, private databases, and subscription-based resources, contributing to a broader yet less visible realm on the internet. However, while visiting the dark web itself isn’t against the law, engaging in illegal activities there is. The dark web contains a range of content, some of which is illegal, including marketplaces for drugs, weapons, stolen data, and other illicit services. The dark web presents various threats, including malicious software and computer viruses, posing risks to users’ systems and data security. Users also face the potential danger of government monitoring and surveillance — or scams and fraud, and other activities that can lead to financial loss and identity theft.



