The anonymity provided by the Dark Web makes it an attractive platform for criminals to operate, as it reduces the risk of their identities being exposed. While the Dark Web hosts legal and legitimate content, such as privacy-focused forums and whistleblower platforms. But, it is also known for the notorious illegal activities like black market for drugs, selling of stolen data, and hacking services.
How Do I Get The Tor Browser?
- One of its key benefits is unlimited bandwidth, which sounds awesome and allows for unlimited dark web browsing.
- Tor Browser has an official Android app if you want to use it on mobile.
- Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter.
- Naval Research Laboratory mathematicians and computer scientists in the mid-1990s.
It tends to conjure vague notions of bad people secretly doing bad things. But while it certainly is a place where illegal activities are facilitated, it can also be a force for good. A lot of the user data that gets stolen or leaked from big platforms ends up on the dark web, where users buy, sell, and exchange it among themselves.
Do I Need A VPN To Access The Dark Web?
Freenet is still an experiment designed to resist denial-of-service attacks and censorship. We highly recommend employing another layer of security via a VPN. Another vital precaution is to ensure that your .onion URLs are correct. Onion URLs generally contain a string of seemingly random letters and numbers. Once you are certain that you have the correct URL, save it in an encrypted note—the Tor browser will not cache it for later.

Popular Dark Web Search Engines And Sites
You can find sites like Facebook, Wikipedia, e-commerce sites, YouTube, and more here. RiseUp is a top dark web website that offers secure email services and a chat option. It was created in 1999 as a secure communication platform for people and groups working on liberatory social change. The platform is protected from government interference and malicious attacks to protect the user.
What Is The Hidden Wiki?

You can use these dark web investigation tools to check if your company’s data is available on the dark web. Like Freenet, I2P has its own dark web that consists of websites ending in b32.i2p. For instance, your email inbox, online banking account, or a company’s internal database resides in the deep web. To access these resources, you need to log in with a username and password using a traditional browser like Chrome or Safari. In this way, your browsing experience is made as anonymous as possible – if someone was ‘watching’ you, so to speak, all they’d be able to see is that you’re using Tor. For information about this, check out our guide on how to get on the dark web.
The most common and user-friendly way to access the dark web is by using the Tor Browser, a privacy-focused web browser that allows you to visit .onion websites. Merely exploring the dark web out of curiosity or for research purposes is typically not a problem. PIA is popular in the USA because it offers servers in all 51 states. People in the United States and abroad can use it to venture into the dark web in privacy. With RAM-based servers in 90+ countries and features like WireGuard, IPv6 leak protection, and a kill switch, worries are over. This allows you to go online anonymously and without ISP monitoring.
- If you’re interested in marketplaces, start by learning about the top darknet markets.
- The dark web often connotes illicit activities like illegal drug sales and hacking.
- This protocol, a layer built atop the traditional internet layer, routes communication between random servers (called nodes or relays) to obscure the source.
- Silk Road became one of the most famous online black markets on the dark web for illegally selling drugs.
- Then, simply click the operating system that you are using and download the file.
Search The Web
It includes media and archives which cannot be crawled and indexed with current search engine technology. This part of the internet is notorious for illegal activities, facilitated by the anonymity it offers. Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses. The Dark Web, despite its association with criminal activities, serves as a platform for individuals seeking privacy and protection.
Risks Of Accessing The Dark Web:
One of the major advantages of the Dark Web is the maintenance of “Privacy and anonymity”. Journalists, activists and others use the Dark Web to communicate safely and anonymously to avoid censorship. Platforms like SecureDrop provide a safe space to communicate and share information anonymously. The anonymity surrounding Dark Web makes it both intriguing and controversial since people argue about its ethical and legal boundaries. Government authorities and cyber security professionals continuously observe this untraceable domain to detect and report cyber offences. But advocates defend its usage as a necessity for people living in oppressive countries.
It offers outstanding privacy features and is currently available at a discounted rate. When you open your default browser, Freenet will be ready and running through its web-based interface. Note you should use a separate browser than the one you normally use to help ensure anonymity. For a number of technical reasons, it’s much faster and more reliable than Tor. The peer-to-peer routing structure is more advanced, and it does not rely on a trusted directory to get route information. I2P uses one-way tunnels, so an eavesdropper can only capture outbound or inbound traffic, not both.
Different Layers Of The Internet

By leveraging these resources and staying connected with professional communities, you can keep abreast of evolving technologies, threats, and best practices. Remember that good judgment, ongoing education, and constant vigilance are your most powerful tools for maintaining a safe and private Dark Web experience. Unlike Tor, I2P is designed for peer-to-peer services like file sharing, email, forums, and even decentralized websites — all within its own closed network. Its distributed nature makes it more resistant to central points of failure. VPN-over-Tor breaks dark web compatibility, reintroduces trust in the VPN provider, and creates unnecessary complexity.
Limit Tracking On The Tor Browser
This is one of the reasons why it is always good to hide your IP address. Sometimes, they even know more than you would like about private matters, such as your health or finances. As much as the Darknet contains even the “good” stuff, it’s not a place you need to stumble about blindly without proper dark web safety.
There’s plenty of illegal content, products, and services available on the dark web. Anonymity doesn’t make carrying out illegal acts any more permissible, so be cautious about making purchases or downloading content. The dark web has a reputation for being a lawless digital underworld filled with criminals and illicit activities. While it’s true that illegal transactions happen there, the dark web itself isn’t inherently illegal.
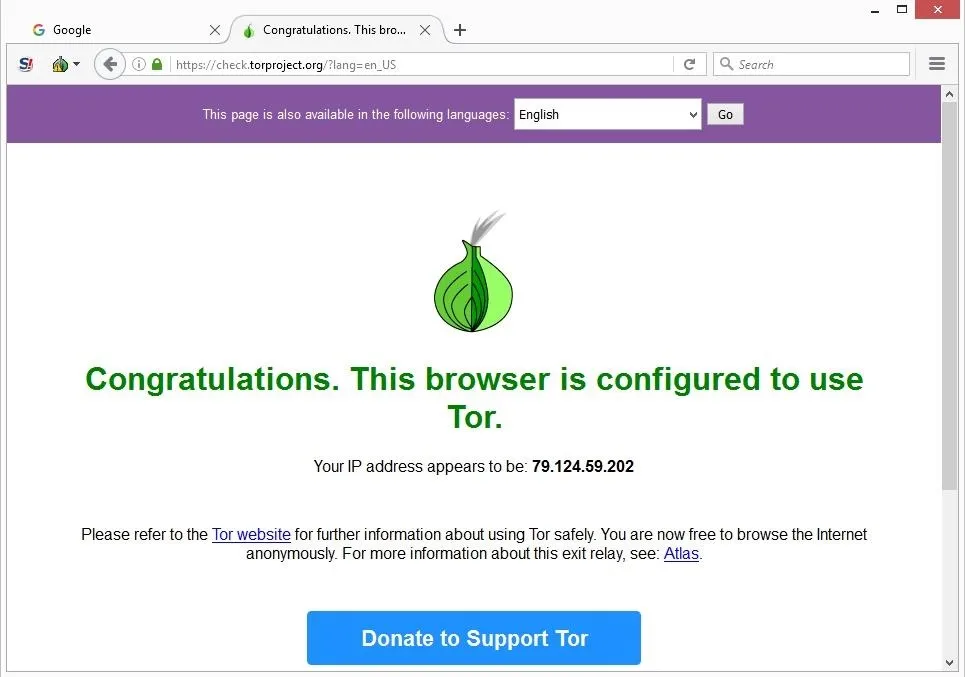
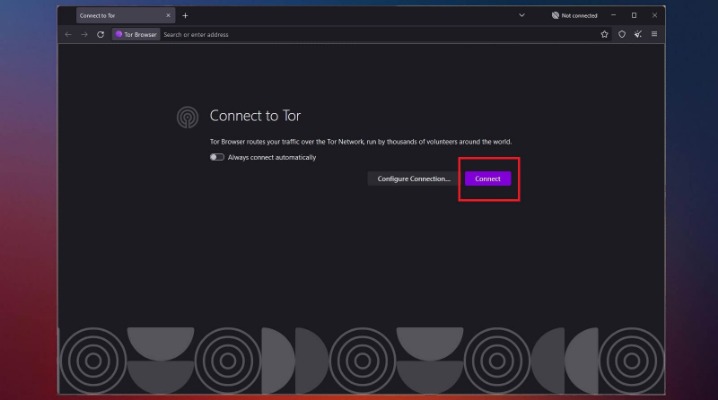
The tradeoff is that you don’t get personalized search results, as DuckDuckGo doesn’t collect user data. But this tradeoff is worthwhile when seeking to browse with the utmost privacy. With your Tor connection established, you can begin surfing the web with the utmost privacy. Like standard browsers, Tor has an address bar where you’ll type the domain you want to visit. To surf the web privately, you need to connect to the Tor network from your browser. Manually implies clicking the Connect button each time you open Tor, while automatically means an automatic connection whenever you open the Tor browser.



