People often have bad feelings about the dark web, but not everything on it is illegal or dangerous. In fact, journalists, privacy advocates and academics use it every day to protect their identities and get to material that has not been blocked. Yes, Tor offers a portable version that can run from USB devices. Tor anonymizes by bouncing traffic through relays; VPN encrypts and routes through a single server. Secure communication for journalists, accessing privacy-focused forums, and whistleblower submissions.
Quick Guide: Access The Dark Web Safely In 3 Steps
It is crucial to approach the dark web with caution and understand the risks involved. Engaging in illegal activities can lead to severe consequences, and exposing personal information or engaging with malicious individuals can compromise your privacy and security. The dark web is often misunderstood due to the illegal activities that occur within its depths. However, it’s important to note that not everything on the dark web is illegal. Journalists, activists, and individuals concerned about privacy and censorship often use the dark web to communicate securely and anonymously. Nevertheless, caution should always be exercised when venturing into this hidden realm.
Is It Illegal To Go On The Dark Web?
Use different passwords for each account so that a single compromised account doesn’t affect others. Tor doesn’t support external plugins and extensions, unlike standard browsers. This addon allows you to control which sites can executive JavaScript and which ones can’t. Tor blocks JavaScript by default, but this addon lets you permit it for trusted sites. The same applies to downloading files, which often contain tracker elements. You should avoid downloading files via Tor to maximize your anonymity.
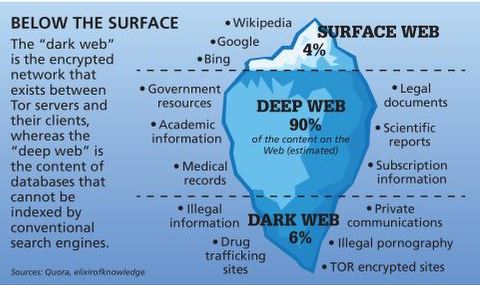
The Three Layers Of The Internet
You can also run a dark web scan to see if your information has been leaked on the dark web. This dark web monitoring will help you track illicit activities and minimize the risks of cyber-attacks. The dark web is a hidden part of the internet that isn’t indexed by traditional search engines and requires special software like Tor to access. It’s often used for anonymity, both for legitimate privacy reasons and for illegal activities like black market trading or data leaks. Torch is one of the more established dark web search engines, designed to help users navigate the Tor network and discover onion sites. Unlike traditional search engines like Google or DuckDuckGo, Torch indexes hidden websites that operate beyond the reach of the surface web.
You may already be aware that malicious actors can use these to harm your credit, engage in financial theft, and breach of your other online accounts. Leaks of personal data can also lead to damage to your reputation via social fraud. Yes, simply accessing the dark web is legal in the United States.
Tor routes data through at least three servers, and websites will only see the IP address of the last server, not yours. It has features to maximize your privacy, unlike standard web browsers that have less stringent privacy protections. However, using Tor has some challenges that you should be prepared for. Darknet marketplaces can be surprisingly similar to sites you find on the surface web—complete with limited-time sales, customer reviews and advertisements for organic products. However, criminals use these marketplaces to sell illegal products and services, including drugs, weapons and hacking software. Many identity thieves and hacking groups make money selling the information they steal on the dark web.
- Unlike other search engines, it does not collect or share web activities and personal data of users.
- These websites use special encryption protocols and are accessible only through anonymizing tools like the Tor Browser.
- The spy agency is hoping to securely and anonymously collect tips, though its entire website, including job listings, are available on the onion service.
- These websites will now work without issues, as the VPN hides the exit node and makes your traffic look inconspicuous.
Examples include password-protected websites, private databases, and subscription-based resources, contributing to a broader yet less visible realm on the internet. The Open Web, also known as the surface web, constitutes the most accessible layer of the internet, readily navigated through popular search engines like Firefox, Google, Bing, and Yahoo. It encompasses public domains such as websites, social media platforms, news sites, and online stores—content accessible to anyone with the help of the internet and a web browser. Put simply, the deep web is all the information stored online that isn’t indexed by search engines. You don’t need special tools or a dark net browser to access most of the deep web; you just need to know where to look.
Look no further if you want good music while navigating the dark web. Deep Web Radio is a digital station with a wide variety of music. The .onion site has thousands of downloadable comic books ranging from niche to mainstream. As with the Imperial Library, you should be aware of copyright infringement. Another notable security trick Wasabi uses to verify transactions is the Neutrino protocol. It assigns a task to the client instead of the server, eliminating server-related vulnerability.
Top 10 Best Dark Web Search Engines In 2025 Safe &
Everything else, from academic journals to private databases and more illicit content, is out of reach. This deep web also includes the portion that we know as the dark web. In the U.S., dark web usage has been growing steadily—not just among cybercriminals, but also among privacy-conscious users.
- Avoid using the same password across multiple sites since it increases your vulnerability if one account is compromised.
- Leaks of personal data can also lead to damage to your reputation via social fraud.
- You could consider the clear or surface web the “top” and visible layer of the internet, easily accessible using a browser such as Safari, Chrome, Edge, or Firefox.
- In this instance, too, it is important to use a logless VPN and pay with Bitcoin if you can to stay anonymous.
- However, it’s important to understand that no system or practice can offer absolute security.
The Biggest Crypto Exchange Hacks: How To Make Sure You Protect Your Crypto Against Hacks

Also, your data is more likely on the deep internet in one way or the other. But you have to keep your fingers crossed that it remains there and hope the party holding your data (the school or hospital records department) keeps it according to the GDPR standards. As a matter of fact, your data could be anywhere on the internet, meaning it could already be at the three internet levels (surface web, deep web, and dark web).
The Tor Browser – What Is It?
Tails (The Amnesic Incognito Live System) is a Linux‑based operating system that boots from a USB stick and routes all traffic through Tor. It leaves no forensic trace on the host computer, resets to a clean state at every reboot, and includes VeraCrypt, KeePassXC and OnionShare for secure file handling. Use Tails when the stakes—journalistic work, whistle‑blowing, sensitive research—justify a fully compartmentalized environment. A cautious setup minimizes the chances of leaking your identity or infecting your device. Follow these four essential steps before you click a single .onion link. Sellers migrate to invitation‑only channels or switch to encrypted messaging apps when a site goes dark; buyers follow reputation scores, not domain names.

This is why many people prefer an identity theft protection service and a financial and credit fraud protection solution. By doing so, early signs of fraud can be detected in near-real time, such as new inquiries on your credit file like new credit cards or bank loans. Although browsing the dark web is not illegal, it contains unsavory activities that can expose you to danger. Remember that any website engaging in illegal activities such as drug trafficking, weapons sales, hacking, and human trafficking violates international laws and, therefore, is illegal. Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and trojan horses.

These search engines work best if you already know what site you’re looking for, not for general browsing. Established in 2012, the platform is a time capsule that collects snapshots of websites. These onion addresses will remain online even if the original page disappears. It also keeps the graphical copy and text of the page for better accuracy. The BBC news website has a special .onion site, which you need to access via the dark web. Its goal is to offer anonymous access to the content without being censored, no matter where you live.
That means that when Tor is compromised, or perhaps there’s a new vulnerability exploit in the Tor network, a VPN will still protect your privacy. The compromised Tor exploit might trace back to you, but then again, your VPN will lead it somewhere else – which makes it impossible to be traced back to you. It’s not a secret that ISPs (Internet Service Providers) and the FBI are tracking Tor users.



