
While some reports of dark web murder-to-order are overblown, it is possible to commission acts of cybercrime on the dark web. These range from phishing campaigns to DDoS (distributed denial of service) attacks, which can take down entire servers and websites. Many dark websites are set up by scammers, who constantly move around to avoid the wrath of their victims. Even commerce sites that may have existed for a year or more can suddenly disappear if the owners decide to cash in and flee with the escrow money they’re holding on behalf of customers. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below.
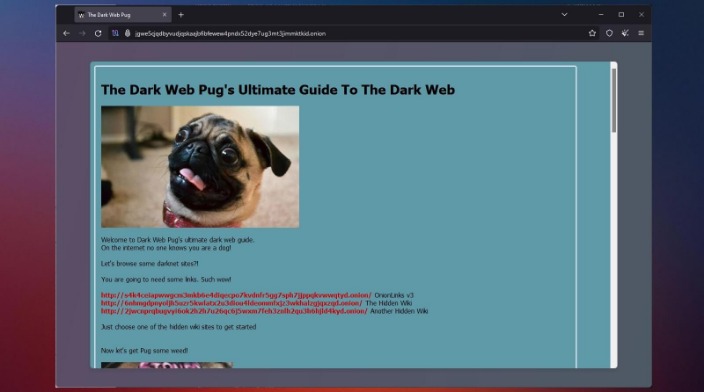
The best thing to do is get your hands on some good darknet directories to find secure pages regarding the stuff you want to search for. The dark web itself has a lot of dark web site directories to help you point out where you need to go. When accessing the dark web, the last thing you want is to leave traces behind that could be traced to you. Setting up the Tor and VPN separately is recommended if this is a concern.
However, it also lingers all across the dark web to infect unsuspecting users just like it does on the rest of the web. The dark web refers to sites that are not indexed and only accessible via specialized web browsers. Significantly smaller than the tiny surface web, the dark web is considered a part of the deep web.

Potential Malware
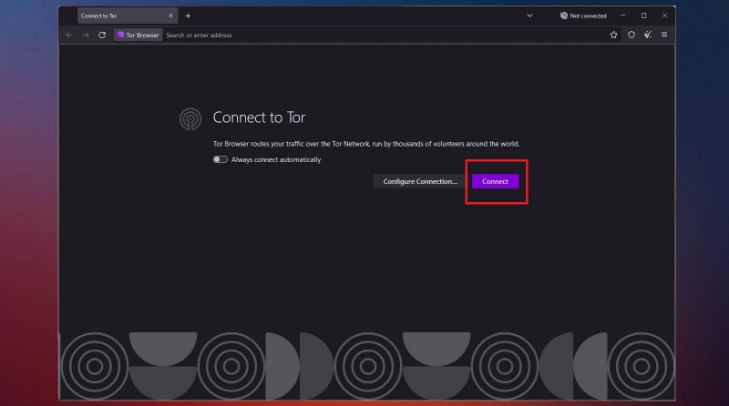
The nearest server will typically provide the fastest and most stable connection speeds. Upon opening the Tor website, you will be presented with various download options for the operating systems that Tor supports, including Windows, macOS, Linux, and Android. In contrast, VPN over Tor setups won’t protect your real IP address if Tor leaks, require more technical setup, and aren’t supported by many VPN providers. For totally hiding all of your online antics, you’ll want to also use a VPN.
Risks And Dangers Of The Dark Web
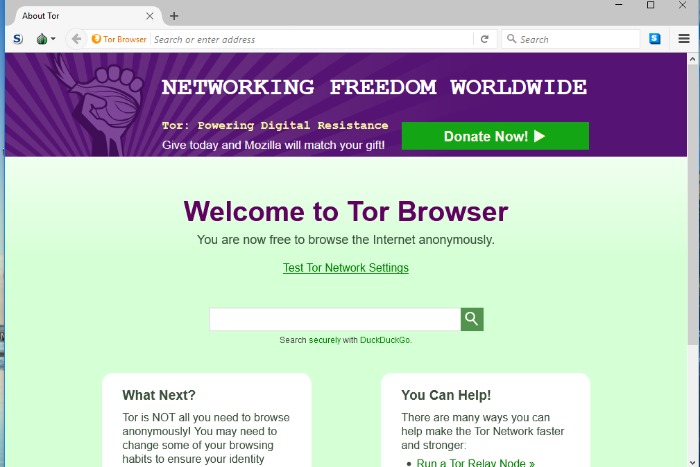
He has also contributed to platforms like Financesonline.com and Timeero.com. “Forest VPN gave me the confidence to explore the dark web for research purposes without fear of exposure.” — Alex T. Schedule a demo to see how Cyble can protect your brand from dark web threats. Based on Mozilla’s Firefox, this browser hides all that pinging about in the background. “It’s a web browser. Use it like one. It’s that simple,” says Muffett. That’s the desktop edition, but there’s a version for Android and an unsupported onion browsing app for iOS.
Understanding BlackCat Ransomware: Threat Overview And Protective Measures
Sections of the dark web are often closed down too, as part of police operations. The deep web is just the part of the internet you can’t find with a search engine. It’s not mysterious or spooky; it’s home to everyday things like scientific research, medical records, private financial information, and secure communications. If you’re interested in marketplaces, start by learning about the top darknet markets. These platforms are hubs for various services and goods, and understanding their features is key to navigating them safely.

Is Tor Browser Free?
There are a few reasons why the dark web isn’t stopped or shut down. First, it’s difficult to track and monitor activity on the dark web since much of it is encrypted. The dark web allows people to access and share all sorts of illegal and explicit material without judgment or censorship.
Can I Use Tor To Browse The Surface Web?
Remember, the dark web can be a volatile and unpredictable environment, so exercising caution and maintaining a proactive approach to cybersecurity is essential at all times. By following these tips, you will be better equipped to navigate the dark web effectively and make the most of your DuckDuckGo search experience. Explore this FAQ section to get answers to some common queries about this hidden part of the internet. Secure your online accounts with unique, strong passwords that are difficult to crack, such as a combination of uppercase and lowercase letters along with numbers and special symbols.
- The Deep Web includes unindexed content like private databases and password-protected sites accessible with standard browsers.
- This means your activities cannot be traced or your browser history exposed.
- Use Tails when the stakes—journalistic work, whistle‑blowing, sensitive research—justify a fully compartmentalized environment.
- This will help you navigate the dark web safely while staying out of markets you don’t want to come across or engage with.
- By distributing communication over several nodes, it obscures the user’s IP address.
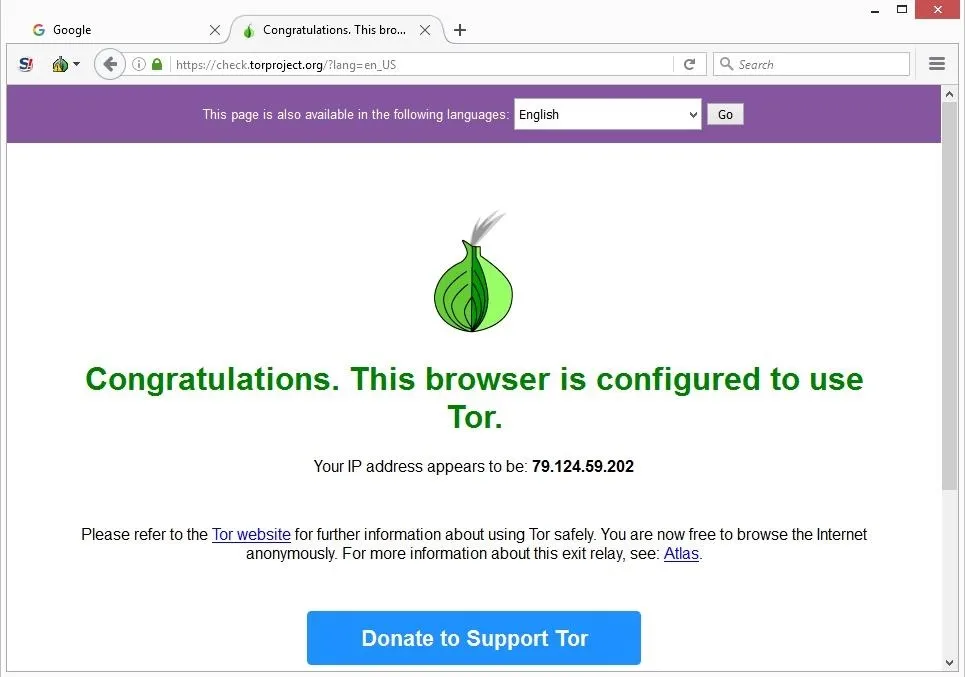
Can My ISP See That I Am Accessing The Dark Web?
You should never trust websites and forums on the dark web with your personal information. You can check our guide on the best VPN services to find the right VPN solution to protect your privacy. Though the dark web offers anonymity for journalists and activists in oppressive regimes, it raises many ethical concerns. These tactics trick users into revealing sensitive information or paying for non-existent products. Like Freenet, I2P has its own dark web that consists of websites ending in b32.i2p.
Get Avast BreachGuard for Mac to protect your privacy and keep your personal data from falling into the wrong hands. Get Avast BreachGuard for PC to protect your privacy and keep your personal data from falling into the wrong hands. Avast BreachGuard monitors the dark web for data breaches around the clock. If a breach is detected, BreachGuard will notify you right away and help you take the steps you need to secure your data immediately. By monitoring known dark web marketplaces, Avast BreachGuard will alert you immediately if and when your data is found. That way, you can change your passwords and lock down your accounts to help block scammers from using your data against you.
- These markets operate similarly to physical drug markets but are hidden from law enforcement through the use of the Tor network.
- Moreover, the company also uses HTTPS and SSL encryption on the Onion site for extra protection.
- These computers are all owned by volunteers, passionate about privacy and happy to offer up their device to help others.
- It also has 10 simultaneous connections, support for all devices, and server obfuscation that works in China.
By leveraging these resources and staying connected with professional communities, you can keep abreast of evolving technologies, threats, and best practices. As digital landscapes evolve, so do the methods of accessing hidden content and maintaining anonymity. While the Dark Web remains a core venue for privacy-seeking users and covert activities, a range of emerging platforms and shifting trends shape the broader ecosystem of underground communication. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node. Though no one should bat an eye just because you’re attempting to access the dark web, keep in mind that in some countries, like the United States, even a simple foray can get you in trouble.
Remember only to make purchases using digital currencies and never provide any online banking login details. Now that you’re connected to Tor, you’ll need a dark web search engine to help you find .onion sites. Unlike regular websites, .onion sites have complex, hard-to-remember URLs that you can’t find using regular search engines like Google. As such, it’s important to be extremely careful when accessing the dark web, as you could inadvertently access a site containing, displaying, or linking to illicit content in some form.



