
For example, legitimate sites, such as the BBC, the New York Times, ProPublica, and Facebook, have made their sites accessible as a Tor Onion URL to help people avoid government censorship. These sites are only accessible over the Tor network and are commonly used for privacy and anonymity. The Tor Browser also features many built-in protections that protect against tracking and fingerprinting. You can conduct discussions about current events anonymously on Intel Exchange. There are several whistleblower sites, including a dark web version of Wikileaks. Pirate Bay, a BitTorrent site that law enforcement officials have repeatedly shut down, is alive and well there.

Here are our favorite choices that work well and support Tor Over VPN perfectly. This method is far more complex but we’ll still explain it for those too curious. As opposed to the previous situation, here, you’re first connecting to Tor and then the VPN. Not many providers support this, so a manual and sometimes tedious configuration is needed.
Wrap-Up: Staying Safe While Accessing The Dark Web
Some whistleblowers and journalists use these portals to safely leak information, especially when a source requires complete privacy. Some markets even sell privacy tools, but you are more likely to run across counterfeit prescription pills and stolen identities. Some markets are relatively short-lived (thanks to law enforcement), but others are notorious enough that they survive, for instance, Silk Road, AlphaBay, and Hansa.
Is It Illegal To Visit The Dark Web?
By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. Tor traffic is decrypted at the exit node, which opens a vulnerability for malicious actors to inject malware or intercept traffic. Hence, it’s advisable not to download files via Tor, especially from unknown sources. Tor is slower than standard browsers because it routes your traffic through multiple servers. This routing, through at least three nodes distributed worldwide, introduces latency, especially when there’s congestion on specific nodes.
Tor-over-VPN Vs VPN-over-Tor: The Right Order
A handful of dark web search engines that do index .onion sites include NotEvil, Ahmia, Candle, and Torch. Tor is a network of volunteer relays through which the user’s internet connection is routed. The connection is encrypted, and all the traffic bounces between relays worldwide, making the user anonymous. Among the many benefits of using a VPN vs a proxy or Tor is that it provides full encryption for all the data you send and receive online. So not only is your web activity hidden, but you can mask your IP address by connecting via a wide range of global VPN server locations.
Which Is The Best Laptop For Cyber Security Course?
- The Tor network combined with a VPN is one of the safest ways to get on the dark web.
- For individuals living under oppressive regimes or anyone needing to communicate away from the watchful eyes of surveillance, the dark web is a valuable tool.
- However, note that the site only uses non-sensitive and public data for the metrics.
- However, if you must buy items from the dark web, set up a secure, encrypted email with CounterMail or ProtonMail.
When you’re done surfing or shopping on the dark web, don’t forget to shut down Tails. The major advantage of using a live OS such as Tails is that, on shut down, the OS wipes itself from the thumb drive you’ve installed it. Sure, it’s not as secure as the clear web version, but it’s there and totally legal to use.
Instead of relying on traditional domain name system (DNS) servers, onion websites use cryptographic keys and hashes to generate their URLs and establish connections within the Tor network. With the Tor Browser successfully installed and connected to the Tor network, you are now ready to start browsing the Dark Web. Type onion website addresses ending in .onion into the Tor Browser’s address bar to access hidden websites on the Dark Web. By utilizing a VPN and the Tor Browser, you can ensure a higher level of anonymity and security when accessing the Dark Web. Remember to choose a reliable VPN service, follow the recommended security practices, and exercise caution while exploring this hidden part of the internet.
Is It Safe To Log Into Accounts While Using A VPN And Tor?

Cryptocurrency Transactions Transactions on the Dark Web predominantly occur using cryptocurrencies, such as Bitcoin or Monero, which provide a certain level of privacy and untraceability. The decentralized nature of cryptocurrencies allows individuals to engage in anonymous and non-censored transactions, making them suitable for conducting illicit activities on the Dark Web. In the United States, federal laws like the CFAA provide a broad framework for prosecuting cybercrimes, including those on the dark web. States may have additional statutes addressing specific cyber activities, creating a layered legal environment.
Should I Only Use A VPN To Access The Dark Web?
If you must download something, scan it with antivirus software and consider using a separate device or virtual machine. You should also avoid clicking on suspicious ads or pop-ups, as they may contain malware or lead you to scam sites. Even if they aren’t actively malicious, they might still have weak security or expose you to threats. Additionally, make sure that you only download the Tor Browser from the official website. Open the VPN app and connect to a nearby server before launching the Tor Browser, and that’s it!
How To Get On The Dark Web Using Tor Browser
Journalists, whistleblowers, and activists often use the Dark Web to communicate securely and share information that could be censored or lead to dangerous consequences if exposed. In short, even with Tor, there’s no perfect anonymity online, but there are efforts to claw back our power online, says Lewis. Using the Tor browser is simple, but knowing when to fire it up is more complicated.
- On top of that, Tor’s nodes can also malfunction because they’re owned by volunteers, which will expose your traffic and sensitive information.
- While you can visit the obscure part of the internet without a VPN, it’s better to go with one.
- Onion links are URLs that end with .onion and can only be accessed through the Tor network.
- You’ve probably heard that Tor makes you anonymous on the dark web — but that’s only half true.
- Another essential security feature is that all incoming and outgoing data from the app is encrypted, including any private and public keys involved.
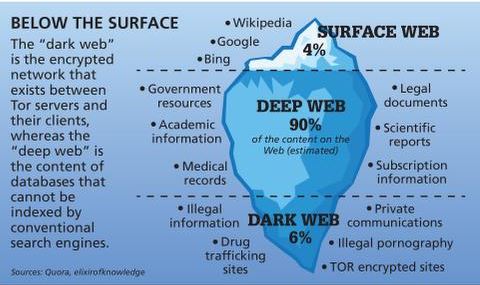
It is a subset of the Deep Web, which includes any web content that is not indexed by search engines. While the Deep Web consists of legitimate platforms such as online banking portals or password-protected websites, the Dark Web is where anonymous and illicit activities typically take place. Accessing the dark web is not inherently illegal in many jurisdictions. It is a part of the internet that requires specific software, such as Tor, to access. This software is legal and often used for legitimate purposes, including privacy protection and circumventing censorship. The legality of accessing the dark web depends on the activities conducted while on it.
However, not all countries are signatories, limiting their effectiveness. Jurisdictional differences significantly impact the legal interpretation and enforcement of dark web activities. The global nature of the internet means laws and penalties vary widely between countries, creating a complex legal landscape for users and law enforcement. Understanding these differences is crucial for cross-border investigations or cases. Internet traffic is secured using adjustable levels of encryption. You can choose 256-bit for maximum protection or 128-bit if you want a faster connection.
Stay Informed On Security Issues
Its goal is to offer anonymous access to the content without being censored, no matter where you live. The good news is that the BBC Onion site is an international edition. As a result, it not only focuses on the UK but also provides worldwide news.



