The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a SHA512 authentication hash and 2048-bit DHE-RSA key exchange. While NordVPN is undoubtedly a great service, it’s not without fault. In 2018, someone gained access to a third-party data center in Finland.

Moreover, due to its popularity, many copycats of the Hidden Wiki exist. So don’t be surprised if you encounter different versions that claim to be genuine, and be very careful. Purchases through links on our pages may yield affiliate revenue for us. We review and list tools and products without bias, regardless of potential commissions. A VPN can help disguise your use of Tor and your visits to dark web resources.
It then depends on you, as the user, how you surf the dark world. To access a dark web resource, you will need to know its web address to the letter. These websites will also use .onion top-level domain names, and many of them will be very long, random combinations of letters and numbers. You won’t be able to access .onion addresses using a standard search engine as they aren’t indexed by crawlers. VPNs are also used for accessing geo-locked content hosted by streaming services. The best VPN options are paid-for and subscription-based, as many free options will either throttle your speed or collect your data.

Be Cautious With Downloads

Crimes range from data theft and selling illegal goods for cryptocurrencies to human trafficking and more severe offenses. The dark web isn’t entirely bad, but it’s clear that it can be deeply dangerous. It’s a hotbed of crime — both physical and digital — and anyone who dares enter it would be exposing themselves to those dangers. That’s why, as cybersecurity experts and safety advocates, we don’t recommend accessing the dark web.
Official Websites And Documentation
For example, many things can go wrong if you try to change any settings inside the browser, including exposing your private browsing information on the dark web. But if you still want to crack on, we’ve previously looked at how to install and use the Tor browser and find onion sites you can visit without getting into trouble. In this case, you connect the VPN service and then launch Tor Browser. Your gadget’s internet traffic routes through the VPN’s provider server first and then via Tor Network before it reaches the destination website. Thus, your ISP does not realize you’re using Tor because they only view encrypted VPN traffic. Using a VPN obstructs your privacy and specifies an entry node, and a VPN with an obfuscation feature makes it look like to your ISP that you are browsing the regular web.
How To Access The Dark Web Using Tor?
- For the most security-conscious, you can even install the Tails operating system on a flash drive and run Tor from that.
- The browser is available for Linux, macOS, and Windows desktop and laptop computers.
- You’ll need an overlay network to facilitate your dark web access.
- It’s a part of the internet that’s less regulated and more shadowy, for better and for worse.
- Not all dark web services are genuine, and many scam “.onion” sites offer downloads infected with backdoors and trojan horses.
With this setup, your ISP sees Tor usage, and your VPN provider sees the final traffic after it leaves Tor. Perhaps the best-known thing you can buy on the Dark Web is information collected in what seems like the almost daily data breaches we read about in the news. That information can include checking and credit card account numbers, social security numbers, and other sensitive information. In darknet mode, you can select friends on the network and only connect and share dark web content with them.
Wrap-Up: Staying Safe While Accessing The Dark Web
Embrace these strategies to confidently navigate the Dark Web, preserving your privacy and security in an ever-evolving digital landscape. When you use Tor, which routes your internet traffic through many different relay nodes, your online activity is obscured because you’re browsing anonymously. Connecting to the Tor network might raise eyebrows depending on who and where you are. Although data sent through Tor can’t be tracked or decrypted, your internet service provider and network administrator can still see that you’re using Tor. The VPN’s encryption will hide from your ISP the fact that you’re using Tor.
Government Surveillance
These both use SHA256 for authentication and 2,048-bit RSA keys. There are multiple protocol options available and protection against IPv6 leaks and DNS leaks. The dark web is something of a mystery to the average internet user. It tends to conjure vague notions of bad people secretly doing bad things.
Limit Tracking On The Tor Browser
The dark web offers both benefits and risks for users going into it, but the intent of the user will also impact this. The dark web contains a wide variety of services and content, some of which skirts or disregards legality. Though the intention and purpose of users on the dark web may vary, the dark web itself is neither good nor bad. One of the problems with free VPNs is that they have a poor user-to-server ratio, with too many users and not enough servers. This is not what you want when also using the Tor network, as the two in conjunction will be painfully slow. Its inherent anonymity allows everyone from dissidents to whistle-blowers the opportunity to share information free from persecution.
How To Access The Dark Web Safely Step-by-Step In 2024
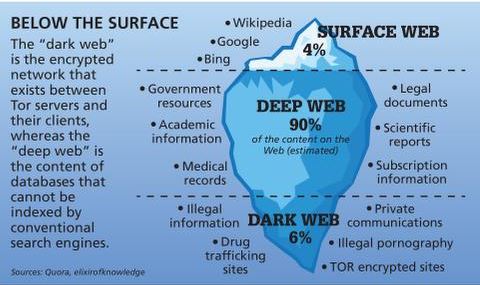
The main purpose of TOR is to provide access to the dark web and bypass censorship and surveillance in countries with restricted internet access. On the other hand, the TOR browser is a web browser that uses the TOR network to offer users private and anonymous internet browsing. Therefore, if a person accesses the dark web with the intention of engaging in illegal activities or purchasing illegal goods and services, they could be committing a crime. Additionally, some countries may have laws that prohibit accessing the dark web or using certain software or configurations to access it. It is important to note that even browsing the dark web can be risky, as there is a high risk of encountering malicious content, scams, and other dangers. The internet as most people know it represents only a small fraction of what truly exists online.
Well, relying on Tor to keep you anonymous online is a good recipe for disaster – we’ll see why soon. Staying cautious is essential when interacting with content on the dark web, as illegal activities are prevalent. Users should refrain from clicking on unverified links and exercise discretion in revealing personal information. The dark web is notorious for hosting a wide range of cyber threats that pose significant risks to individuals and organizations. One common threat is the sale of stolen credentials, including usernames, passwords, and financial information, which cybercriminals use for identity theft and fraud. The dark web operates on specialized networks that require unique software to access, such as Tor (The Onion Router).
Some dark web commerce sites have dangerous chemicals and weapons for sale. The Hidden Wiki is a surface website offering a collection of dark web links. Before visiting any dark websites, get comprehensive cybersecurity software to help protect yourself from threats you may encounter. The Tor network combined with a VPN is one of the safest ways to get on the dark web.



