Unlike carding shops, which primarily focus on the trade of information, carding forums serve a broader purpose within the cybercriminal community. On these forums, actors will often share techniques, hacking tools, strategies, and resources for conducting fraudulent activities. The dark web is a part of the internet that is not indexed by traditional search engines and requires specific software to access, such as Tor. This hidden segment of the web plays host to a variety of sites, including illegal marketplaces that often deal in stolen goods, including credit card information. Dark web posts and offers of this size are usually scams, so the massive dump of cards could easily be fake data or recycled data from old dumps repackaged under a new name. Search queries entered returned large volumes of content that appeared to be useable to perpetrate fraud within the first 20 results, meaning it was widely accessible at just one click.
Legal Analyst Reveals When John Bolton Took A ‘reckless Risk’
These unauthorized transactions might include buying high-value electronics, designer clothing, or gift cards, all with the intent to quickly convert these ill-gotten gains into cash or valuable assets. Alex proceeds to the dark web, where he lists the credit card dump for sale to the highest bidder, often demanding payment in cryptocurrency for anonymity. Another cybercriminal, a buyer, purchases the dump and obtains access to this treasure trove of stolen credit card data. Shadow Market is one of the largest English speaking marketplaces specializing in selling stolen credit cards, credit card dumps with full info such as Track 1 and 2 code, all billing info and CCV2. This marketplace is apparently operated by a former stuff members of the now defunct UniCC Shop.
Check To See If Any Of Your Credit Cards Are Exposed By This Dark Underground Market
Providing detailed information about the attack can help authorities track down the perpetrators and bring them to justice. In some cases, the company may be held liable for damages resulting from the breach, which underscores the importance of having robust cybersecurity measures in place. It is a hub for financial cybercrime and offers a wide range of illicit services and stolen data that cater to sophisticated cybercriminals. This stolen information is then encoded onto a blank card, creating a clone of the original card.
Ready To Explore Web Data At Scale?
- Then, on Dec. 17, an apparent raid by authorities saw several of the carding site’s servers seized, temporarily shutting down the illicit business.
- The notice should include clear instructions on how to protect themselves against identity theft and potential fraud.
- Some fullz even include photos or scans of identification cards, such as a passport or driver’s license.
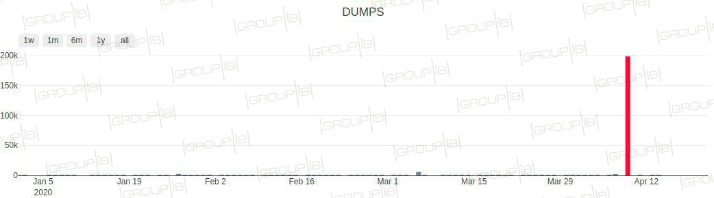
- Threat actors have leaked 1 million stolen credit cards for free online as a way to promote a fairly new and increasingly popular cybercriminal site dedicated to…selling payment-card credentials.
Other sellers offer discounts for buying multiple cards, while the cheapest card — with between US$700 and US$1,000 on it — can cost as little as US$80. The best way to monitor your credit cards is by downloading your credit card company’s app from the Apple App Store and Google Play Store. BidenCash apparently used the free stolen data dump to draw attention for marketing, even using an image of President Biden as its brand identity, as discovered by Cyble researchers who detected the data breach. Based on our observations from analysis on dark web data using Lunar, we’ve identified the top 7 marketplaces on the dark web in 2025.
What Can Be Found On Deep And Dark Web Credit Card Shops?
You can also use virtual credit card numbers for online shopping, which can’t be used again for subsequent purchases. This hack was a massive breach of customer trust, and it’s a stark example of the devastating consequences of a data breach. It’s a wake-up call for all of us to be more vigilant about our online security. It’s a marketplace where sellers offer a range of Credit Card Dumps for sale, often including details like the card’s balance and country of origin. This password unlocked the credit histories and personal information of many Sears customers, which were subsequently used to obtain their credit card numbers. This type of card has been around for decades, with the first credit cards emerging in the 1950s.
What Is Carding In Cyber Crime?
Apart from the dark web markets that are operating online today, some raided platforms influenced many markets. It maintains a very strict level of user verification and integration with an official Telegram account to provide real-time updates to users. Various cryptocurrencies such as Bitcoin and Monero can be used to make purchases. Believe it or not, some dark web marketplaces have pretty advanced systems for building trust. Sellers often need to pay a deposit to prove they’re serious, and they build their reputation through positive reviews.
I’ve investigated too many breaches where malware jumped from an infected office computer to the payment network. Require multi-factor authentication for high-risk transactions, but it needs to be implemented intelligently. This enables systems to detect fraud based on minute changes in transaction velocity, merchant category patterns, and even the time of day purchases are made. Pattern recognition through machine learning has revolutionized how we spot compromised cards.
The Easy Way In/Out: Securing The Artificial Future, Trend Micro Security Predictions For 2025
Not to mention the resulting tarnished reputation, which required extensive post-event damage control. AllWorld Cards has been active since May 2021 and currently holds an inventory of over 2,749,336 credit cards, with an average price per card of $US 6. Card checkers are tools used by threat actors to verify the validity and authenticity of credit card information they purchase on the dark web. The three suspects from Indonesia confessed to stealing payment card data using the GetBilling JS-sniffer family. Canceling your PayPal account or credit card is a crucial step in preventing further unauthorized transactions. Classic darknet markets sell diverse illegal goods; data stores focus on leaked or stolen data like credentials, databases, and ID records.
Dangers And Risks Of Credit Card Dumps
The market for stolen credit card data is vast and constantly evolving, with buyers and sellers from all corners of the world participating in these illicit transactions. In conclusion, Blackpass is a controversial dark web marketplace known for offering stolen credit card information through its dumps. While the site claims to source data ethically, there are substantial risks involved in its use.
Rethinking Vulnerability Management In A Heightened Threat Landscape
Valued at approximately $15 million, Abacus Market is one of the most lucrative platforms in the dark web ecosystem. To expand their reach, some marketplaces established parallel channels on Telegram. This further complicates monitoring efforts because now you need to search for the related Telegram channels and track activity there and on the marketplace itself. And while eggs and everything else seems to be getting more expensive for us, these dark web markets aren’t facing inflation but instead dropping in price. Jeffrey Collins, an FBI Supervisory Special Agent who runs the Cyber Security Task Force said, “websites like eBay.”
With the growing threat from cybercriminals who sell stolen credit card information on the deep web and dark web, businesses need to stay ahead of the game. Over the years several advanced tools have been developed to help track and prevent such fraudulent activities. It is important to note that credit card dump attacks can occur both offline and online. Offline attacks involve the use of counterfeit cards at physical locations, while online attacks involve the use of stolen credit card information for fraudulent online transactions.
The Equifax hack in 2017 exposed personal data of more than 147 million customers, including credit card details. “Since that time, we saw a rise in the emergence of several new debit and credit card shops to fulfill the illicit demand for compromised payment cards.” continues Cyble. By following these measures, you can significantly reduce the risk of falling victim to credit card dump fraud. It is important to stay informed about the latest security threats and continuously educate yourself on best practices for protecting your financial information. Joker’s Stash, believed to be the world’s largest online carding store (a forum for selling and buying stolen credit card data), plans to go offline forever on Feb. 15. Researchers from threat intelligence firm Cyble noticed the leak of the payment-card data during a “routine monitoring of cybercrime and Dark Web marketplaces,” researchers said in a post published over the weekend.
This data enables cybercriminals to commit fraud, resell stolen credentials, and facilitate identity theft. If you suspect that your credit card information has been stolen through a data breach, contact your credit card issuer immediately and request a new card with a new account number. You can also place a fraud alert on your credit report to prevent potential further damage. Additionally, monitor your credit report for any signs of new accounts or unauthorized activity.
The analysts claim these cards mainly come from web skimmers, which are malicious scripts injected into checkout pages of hacked e-commerce sites that steal submitted credit card and customer information. To ensure larger reach, the crooks distribute the collection via a clearnet domain and on other hacking and carding forums. BidenCash is a stolen cards marketplace launched in June 2022, leaking a few thousand cards as a promotional move. N 2025, dark web websites frequently change domains and are often short-lived. Accessing them may require .onion links and the Tor browser, but caution is advised due to legality and cybersecurity risks. Cybersecurity experts should pay close attention to these trends, as they often indicate emerging threats and profit-generating tactics among the cybercriminal forums.



