The path from enumeration to root required chaining multiple vulnerabilities, underscoring the importance of comprehensive system hardening. LinPEAS automates the process of identifying privilege escalation paths. To discover hidden directories and files, Gobuster is deployed with multiple wordlists. The journey begins with a comprehensive network scan to map the available services on Cypher. Nmap, a powerful network scanning tool, is utilized to perform both a full TCP port scan and a service version detection.
WITH can be used to assign the values of expressions to variables. Use MATCH to find entities that must be present in the pattern.Use OPTIONAL MATCH to find entities that may not be present in the pattern.OPTIONAL MATCH returns null for empty rows. Beginners can conquer Cypher on HackTheBox by grasping the basics, utilizing essential tools, and following a systematic approach.
- Deny CREATE USER privilege to create users to the specified role.
- Mastering Cypher involves deciphering encrypted messages, exploring directories, and exploiting server weaknesses.
- Grant TRAVERSE privilege on all graphs and all relationships to the specified role.
- Use extreme caution when visiting any darknet market and never share personal information.
- See both encoded and decoded versions simultaneously for quick verification and adjustments.
CipherLink

Reconnaissance in HackTheBox challenges is crucial as it helps identify vulnerabilities, services, and attack vectors. Understanding the target’s infrastructure through thorough reconnaissance lays a solid foundation for successful penetration testing. Effective reconnaissance minimizes guesswork and enhances the efficiency of subsequent hacking steps. Cypher exemplified common web application pitfalls, including insecure configurations and credential mismanagement.
Create or replace a local alias named database-alias for the database named database-name. Create a local alias named database-alias for the database named database-name. Create a node property type constraint on the label Person and property name, restricting the property to STRING.If a node with that label is created with a name property of a different Cypher type, the write operation will fail. Create a relationship property existence constraint on the type LIKED and property when. If a relationship with that type is created without a when property, or if the property when is removed from an existing relationship with the type LIKED, the write operation will fail. Create a point index on nodes with label Person and property location with the name index_name and the given spatial.cartesian settings.

Custom Code Creation
Grant CREATE DATABASE privilege to create standard databases to the specified role. Grant TERMINATE TRANSACTION privilege to terminate transactions on all users on all databases to the specified role. Grant TRANSACTION MANAGEMENT privilege to show and terminate transactions on all users, for all databases, to the specified role.
Two-Layer Security
Grant ASSIGN PRIVILEGE privilege, allows the specified role to assign privileges for roles. Grant DROP ALIAS privilege to delete aliases to the specified role. Grant ALIAS MANAGEMENT privilege to manage aliases to the specified role. Grant SET USER STATUS privilege to alter user account status to the specified role.
Choose whether you want to encode a message into secret code or decode an existing coded message. The user interface of Cypher market is arguably its least commendable aspect. Despite a recent overhaul, the interface has regrettably deteriorated rather than improved.
Unlock The Power Of Cypher Link And Cypher Mirror With Our Curated Marketplace
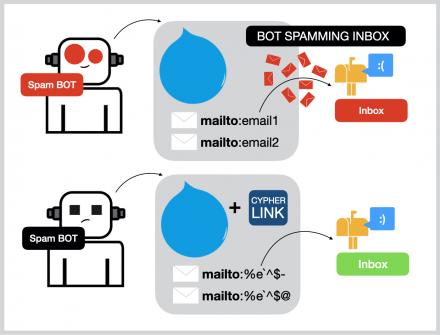
Built for modern infrastructures, this solution integrates seamlessly into your organization’s IT framework, offering a robust shield against data breaches. With respect to Drupal, encryption/decryption of field values happens over ‘Cypher Link’ field-formatter. And currently, it has support for Links, Email, Text and Integer field types. Cypher Link is a decentralized crowdfunding platform designed to empower indie developers by facilitating transparent and cross-chain funding transactions. Built using ThirdWeb SDK, ReactJS, Ethers, and TypeScript, Cypher Link aims to revolutionize the way developers connect with supporters and receive funding for their projects through the use of cryptocurrency.
Tor Darknet Market
Grant SHOW TRANSACTION privilege to list transactions on all users on all databases to the specified role. Deny CREATE NEW TYPE privilege to create new relationship types on all databases to the specified role. Set the default Cypher version for a remote database alias when creating it.
Compliance Ready
- From grapes Southern Rhone White Blend, Pinot N Stores and prices for ‘Sine Qua Non Cypher, California’ prices, stores, tasting notes and market data.
- Deny CREATE NEW TYPE privilege to create new relationship types on all databases to the specified role.
- Calls inside a larger query always requires passing arguments and naming results explicitly with YIELD.
- Popular items such as cannabis and stimulants are available, but the market shines in its ‘Other’ fraud section, offering unique guides and tools.
- Despite a recent overhaul, the interface has regrettably deteriorated rather than improved.
Experience the difference a truly exceptional marketplace can make, and let us be your guide to the world of the best cypher website and cypher tor. Our cypher darknet marketplace has earned the trust of customers around the globe, thanks to our unwavering commitment to quality and customer satisfaction. We’ve built a reputation as the go-to destination for the best cypher link products, and our loyal customer base is a testament to our success. Whether you’re a seasoned cypher darknet enthusiast or a newcomer to the world of cypher link, you can trust that our platform will provide you with the best possible shopping experience. Explore our vast selection, secure in the knowledge that you’re dealing with a trusted and reliable marketplace.

The localdatetime.truncate() function truncates the given temporal value to a LOCAL DATETIME instant using the specified unit. The datetime.fromEpochMillis() function creates a ZONED DATETIME given the milliseconds since the start of the epoch. The datetime.fromEpoch() function creates a ZONED DATETIME given the seconds and nanoseconds since the start of the epoch.
Decoded Mystery Messages
Cypher Market has quickly become a notable presence in the darknet marketplace, renowned for its minimalist design that prioritizes a seamless user experience. Upholding stringent ethical principles, particularly in prohibiting certain illegal content, Cypher sets a standard for responsible operation. Despite a relatively small number of vendors, it offers a vast range of unusual and unique items, surpassing traditional market offerings.
Drupal Code Base
Say goodbye to the limitations of traditional payment methods and hello to the future of cypher tor with our blockchain-powered platform. Experience the seamless, secure, and lightning-fast transactions that will redefine the way you think about cypher darknet shopping. Welcome to our comprehensive marketplace, where you’ll find the best cypher link products from the top online retailers. Discover a wide range of high-quality cypher onion items, all handpicked to meet your needs.
I’ve been a loyal customer of this cypher url marketplace for years, and I can honestly say that it’s the best platform I’ve ever used. The selection is unparalleled, and the quality of the cypher mirror products is consistently top-notch. As a forward-thinking and daring initiative in the darknet domain, Cypher Market extends a broad spectrum of products and services, transcending the boundaries of ordinary internet marketplaces. Its intuitive design promotes exploration, yet users are advised to navigate with caution and a sense of moral responsibility given the darknet’s nature. Cypher beckons those in pursuit of a novel and evolving adventure into the deeper echelons of the digital realm. The platform is in a phase of development, with its management team focused on rolling out significant improvements to enhance the user experience.



