As I’ve previously said, it’s a good idea to keep your interactions with the dark web to a minimum, unless you can absolutely trust the people you’re dealing with. You’ll often see a sign in stores that says “look, don’t touch,” and it’s not a bad adage to bear in mind as you navigate around the dark web. For obvious reasons—I don’t want to get you or me into trouble, after all—I’m not going to get too specific when it comes to what you can find for sale on the dark web. A lot of transactions are handled via cryptocurrencies such as Bitcoin, which is relatively (but not completely) private and anonymous. Another private cryptocurrency you’ll find being used is Monero, which prides itself on being untraceable. The dark web, for the uninitiated among you, is a virtual neighborhood beyond the borders of the normal, everyday internet (which includes the website you’re looking at right now).
Thanks to its fast, super-optimized servers, it offers comprehensive support for P2P file sharing, so you won’t have to worry about lags. Moreover, with this much protection, you can access the dark web easily. Many security analysts and guides suggest using a browser like Tor with a VPN for improved privacy. Husain Parvez is a Cybersecurity Researcher and News Writer at vpnMentor, focusing on VPN reviews, detailed how-to guides, and hands-on tutorials.
Never Reveal Any Personal Information
By observing these patterns, they can link a Tor user’s request to a server and reveal their intended destination. Tor is slower than standard browsers because it routes your traffic through multiple servers. This routing, through at least three nodes distributed worldwide, introduces latency, especially when there’s congestion on specific nodes.
I2P offers several advantages over the Tor network, such as faster access to hidden services and support for BitTorrent, and it is generally harder to compromise. It is easier to install on Windows with the Easy Install Bundle (with all necessary components prepackaged). Digital surveillance and cybercrime continue to rise, underscoring the need for disciplined cybersecurity habits. Brave Browser integrates Tor technology directly into its platform, offering users an accessible, user-friendly gateway to the dark web. Users can easily open Tor-enabled private tabs alongside their regular browsing sessions, making it ideal for seamless and secure browsing experiences. Bear in mind too, that your internet provider will be able to see you connecting to Tor nodes, even if it doesn’t know exactly what you’re doing.
Dark Web – Tor Deep Web Infinity Article
You can use Tor without the browser, but the Tor Browser is the most popular and user-friendly way people interact with the protocol. It’s worth noting that sometimes a single organization’s website will include elements of both the surface web and the deep web. Most schools have a comprehensive website providing information about the school’s history, campus location, student body, available programs of study, extracurricular activities, and more. Essentially, any webpage that requires a login is part of the deep web.
How To Install Tor On Windows, Mac, Linux, And Android
Other options are the Freenet and I2P (Invisible Internet Project) peer-to-peer networks, both of which provide censorship-free communications. If you find that Tor is restricted in your current location, you can use a bridge. A bridge creates an obfuscated relay on the Tor network that is not listed in the main directory.
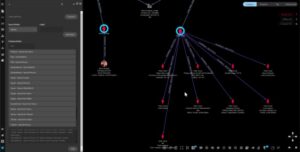
- When you connect to the internet using Tor, your data goes through multiple phases of encryption before it’s directed through a random series of servers called ‘nodes’.
- However, how can you use it if you don’t know how to install the Tor browser on your device?
- Aura’s family plan is also a top rated solution for protecting your children and loved ones from identity fraud.
- Wasabi Wallet is a Bitcoin wallet that not only hides all your data in the Tor network but also allows you to “join” your transactions with others to increase your anonymity.
- The fact that you are using it to visit the Dark web probably makes you even more interesting.
The extra time it takes to load a site is better than your data falling into the wrong hands. Most importantly, the new official Android Tor Browser app will receive frequent updates. That means the official app will receive security and feature improvements.
How To Install And Use The Tor Browser
Additionally, a VPN can enhance security by masking the user’s IP address. By using Tor over VPN, the VPN encrypts your data and hides your IP address. This means that all of your traffic, including your Tor Browser activity, is protected. This does not protect you from malicious exit nodes, as your internet traffic is unencrypted by the time it reaches its destination. Like any other type of app, dark web apps can be safe or unsafe to use, depending on how they are designed and used.
What Are The Differences Between Tor Over VPN Vs VPN Over Tor?
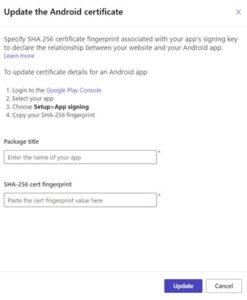
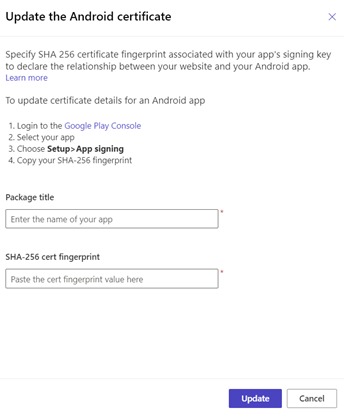
However, with the release of the official stable Android Tor Browser, Orfox will be phased out and stop receiving updates. While there are other dark web browsers, they’re generally unreliable, unsafe, and complicated. The safest way to access the dark web on your phone is by using the official Tor Browser for Android or the Onion Browser for iPhone. Using the Tor Browser is one of the best ways to protect your privacy, especially when combined with a reliable VPN.
What’s The Difference Between The Deep Web, The Dark Web, And The Darknet?
It is simply a network of websites that are not indexed by search engines and require specialized software to access. Just like the regular internet, the Dark Web is a tool that can be used for both legal and illegal purposes. So, what makes the Dark Web so different from the regular internet?

Cybersecurity has to also cover everything physically on your computer too—which law enforcement or government authorities might have the right to seize if they come calling. If you want to be untraceable and undetectable, connecting to the dark web via the Tor browser is a major step towards that, but not the only step you’ll need. To get on the dark web, you need a browser built for the job, and the best in the business is Tor. Tor is a browser engineered for extra security and privacy, and can be used to navigate the normal, surface web as well as the dark web. It blocks trackers, prevents user fingerprinting, encrypts data, and reroutes your browsing so no one can see where in the world you are.
Downloader By AFTVnews
Enjoy the journey, but always prioritize your safety, privacy, and adherence to the law. In the next step, we will discuss some safety measures you should consider to protect yourself while exploring the Dark Web on your Android device. Now that you have successfully downloaded and installed the Tor Browser on your Android device, you are one step closer to accessing the Dark Web.
It’s huge, making up about 90% of the internet, but it’s mostly mundane, hidden behind login screens for privacy and security. Now that you are equipped with the necessary knowledge and safety measures, feel free to explore the Dark Web on your Android device responsibly and with heightened awareness. In the next step, we will explore how to navigate the Dark Web and ensure your safety while exploring this hidden realm on your Android device. Remember, while a VPN can provide enhanced privacy and security, it’s not a foolproof solution. It’s important to use a reputable VPN service and ensure that it is regularly updated with the latest security measures. By taking these precautions and understanding the risks involved, you can navigate the Dark Web more securely and minimize potential harm.