
For businesses, the cybersecurity risks posed by Dark Web marketplaces are substantial. Data breaches, leaked credentials, and intellectual property theft are common occurrences. According to a 2023 study, over 24 billion credentials were circulating on illicit marketplaces, many originating from corporate data leaks. Failing to monitor these underground forums can expose companies to financial losses, reputational damage, and compliance violations. There has been a steady increase in the availability of goods and services offered in the black markets. Greater availability of as-a-service models, point-and-click tools, and easy-to-find online tutorials make it easier for technical novices to use what these markets have to offer.
Access Our Free Web-based Dashboard Or WordPress Plugin
This is a great way to improve your privacy because Tor isolates each website you visit, meaning third-party trackers and ISPs can’t reveal your identity. Keep in mind that you’ve to use very specific keywords when searching. And most importantly, be patient as you’ve to sort through a lot of useless results.
- Accessing the dark web isn’t like surfing the web everywhere else online.
- And most importantly, be patient as you’ve to sort through a lot of useless results.
- The largest component of the S2S network one year before and one year after the operation Bayonet.
- Although the Tor browser has sufficient encryption, combining it with a VPN offers better protection.
- Unfortunately, others are fake and fraudulent websites that exploit the reputation of the dark web to con people.
Legacy And Lasting Impact Of The Silk Road

Lately, the value of BTC has remained around on average $250 USD per BTC for all of 2015 thus far. Using trusted directories, PGP encryption, and secure wallets helps protect against fraud. You can find items like digital goods, software, and even collectibles. Some markets have services related to cybersecurity, while others might list more controversial items.
First Deep Web Black Markets
Nonetheless, if whatever you do is deemed illegal in your country, you can get into trouble. The use of the dark web raises suspicion as it shows there is something you want to do privately. Remember that illegal activities can still incriminate you, whether you are using a Tor browser. For example, you shouldn’t pirate copyrighted material, engage in terrorism, or share illegal pornography. Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts anonymously.
Other Ways To Access Dark Web Platforms
Despite these closures, new platforms continuously rise, adopting advanced security measures to evade detection. The dark web is infamous for containing sites such as Silk Road and other marketplaces where users could potentially buy drugs and/or weapons, stolen credit cards, IDs, and much more. The median net income is positive for sellers while negative for buyers throughout the whole period of observation. In fact, when we compute the total net income for each seller, a considerable fraction (16%) has a negative net income because they spend in markets where they are not classified as sellers, or in the U2U network. Moreover, we find a change of trend between the seller and the buyer median net income time series which reflects the dominance of markets, as detailed in the next section.
Features That Make WTN Market A Secure Platform
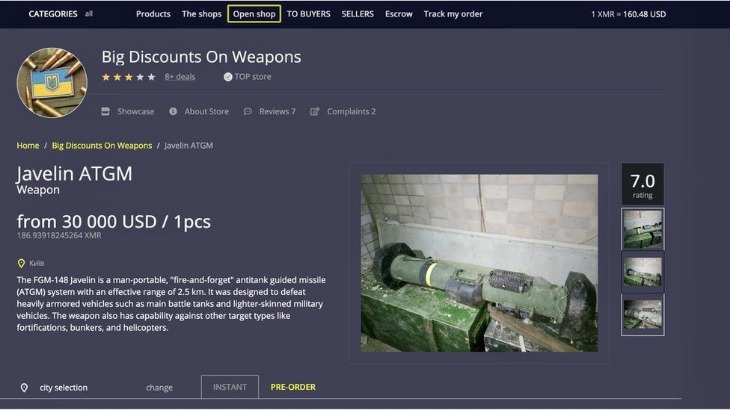
Bazaar marketplace is known for a wide range of products (drugs, fraud tools) and a straightforward interface. It enforces multisig escrow on all transactions and has an active customer support Breaking Bad Forum. Buyers report good uptime (99% monthly) and fast dispute resolution.
Easy Steps To Access Dark Web On Your Phone Safely In 2024
It also masks your IP address, making it difficult for government agencies to monitor or track your activities. We recommend using NordVPN as it offers top-notch security features, including dark web threat protection. Dark web markets have exploded in scale and reach in 2025, becoming the most dangerous hubs for trading drugs, stolen data, and hacking tools. These anonymous marketplaces—operating mainly on the Tor network—are now a primary threat vector for businesses and cybersecurity professionals. In fact, everything is in English, and the site picks up users everywhere in the world. People visit this market to buy stolen credit cards, personal data, remote desktop account credentials, and logs gathered from information-stealing malware.
- Even without the code, you can visit the security section to get tips on improving your daily life privacy.
- As listed above in our article, even respected organizations like the BBC and ProPublica have a version of their site on the dark web.
- Keeper is the first and only password management application to be preloaded with mobile operators and device manufacturers including, AT&T, Orange, America Movil and HTC.
- This marketplace focuses on selling stolen financial data, such as BINs (Bank Identification Numbers), RDP/VDS access, and verified crypto accounts for money laundering.
- Darknet marketplaces may look like regular online stores, but using or even browsing them comes with serious risks.
Unlike the surface and deep web, you can’t access the dark web via a standard or specialized search engine. To access the dark web, you’ll need a specific set of tools – more about that later in the step-by-step section. The dark web (often referred to as the “dark net”, “black web”, or “black net”) is a small section of the deep web that is hidden and kept inaccessible to regular internet users on purpose. That means that only 0.024% of all the known pages are findable in Google’s search engine. The users only have access to a fraction of the available data and web pages. Ransomware leak sites are publicity sites where ransomware groups share the details of their latest victims.
Accessing Darknets
The legality depends on your activities and your country’s specific laws regarding darknet use. You can buy credit card numbers, all manner of drugs, guns, counterfeit money, stolen subscription credentials, hacked Netflix accounts and software that helps you break into other people’s computers. Buy login credentials to a $50,000 Bank of America account, counterfeit $20 bills, prepaid debit cards, or a “lifetime” Netflix premium account.
Exposure To Malware And Scams
The last time I checked, it’s estimated that the entire web is roughly 500 times larger than what Google returns in Google Search. PatrickStash has two categories, Cards and Cards NoVBV (short for Verified By Visa). The site’s forum representative is very active in advertising the shop, touting automatic refunds, live statistics, and sellers in a range of countries as their USPs. However, if someone were to pursue this, here are some safety strategies. First, in the USA, it is a federal offense to use the USPS for any of these transactions.

These hackers don’t hide in the shadows as much as you might think. Anything from planting malware and stealing sensitive files to hijacking email accounts or breaking into social media profiles. Exodus Marketplace started to become popular after the shutdown of Genesis Market, and it replaced it successfully. It claims to control more than 7,000 bots from 190+ countries, with data prices ranging from $3 to $10, based on the quality it offers. The marketplace has a simple interface, lets users filter logs easily, and accepts Bitcoin, Monero, and Litecoin for payments.
Companies must implement strong data security measures, employ encryption, and monitor for data breaches to protect customer and employee information. Darknets and dark markets have propelled the growth of cybercrime by offering a platform for the sale and exchange of malicious tools and services. Cybercriminals use these platforms to traffic in stolen data, execute targeted ransomware attacks, and collaborate on advanced hacking techniques.



