These platforms are hubs for cybercriminals to buy and sell compromised payment card details. In addition to these types of listings, there are other free tools usually available on credit card sites. These tools include for example different types of checkers, which assist threat actors in verifying whether the stolen card information they possess is valid and can be used to make unauthorized purchases.
Collecting Threat Intelligence
Humans, being the slaves of habit, are more inclined to use the same kinds of passwords for most of their accounts. Instead, one must create strong and unique passwords using a password manager. Especially for your banks or financial accounts, the passwords must be strong and unique to that account only. Add your credit card number (along other personal details like email address, phone number, etc.) to the monitoring list. Scammers start by prompting users to download malware, which is often disguised as a harmless email attachment. Once it starts running on your machine, the malware collects data such as used keystrokes, browser history, and shopping habits.

The dark web is a network of websites where people can share information anonymously. Sometimes the activity there is harmless, like when journalists, law enforcement officials and whistleblowers gather and share info without revealing their identity. But it can also be a popular place for identity thieves, who can use the dark web to trade and sell your personal information.
What Are Stolen Credit Cards Used For?
- – Look for a substantial number of feedback and ratings to ensure a more accurate assessment of the vendor’s performance.
- And beware—while many explore out of curiosity or for research purposes, it’s important to remember that engaging with these platforms, even as an observer, can lead to serious legal and ethical consequences.
- Another unique feature Brian’s Club has is the auctions it offers during which users can reserve, bid, and outbid other users who want to purchase exotic BINs.
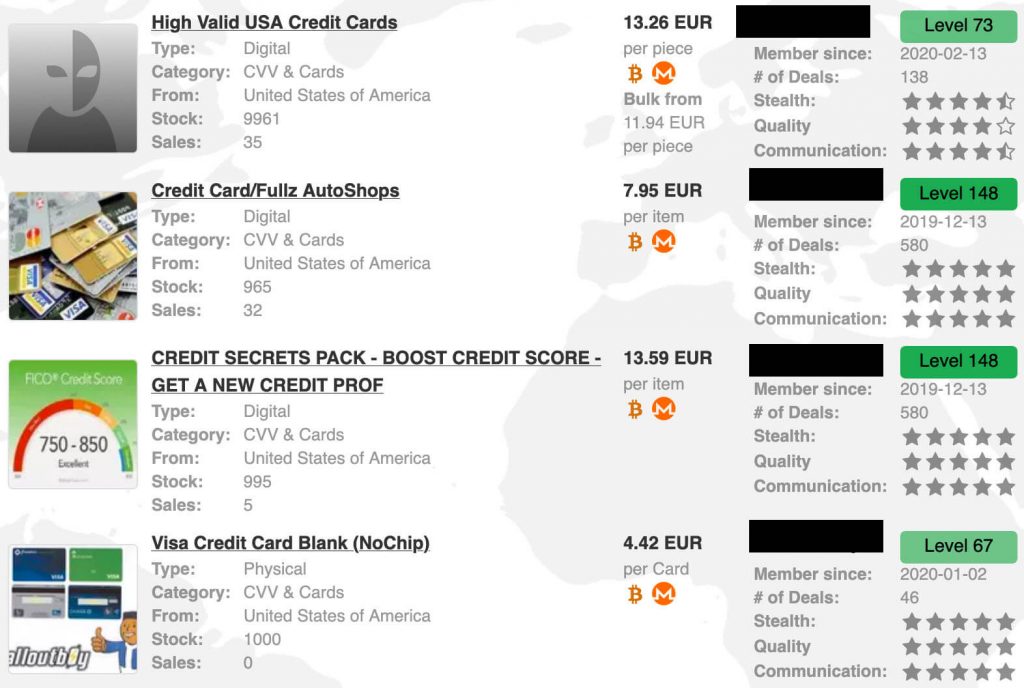
- Full or partial credit card details are commonly sold on the dark web, including BIN numbers, credit card numbers, expiration dates, and CVV numbers.
This incident is described as one of the largest giveaways of compromised credit card data in recent history. If you can, use an online wallet like Apple Pay or Google Pay, says Pascal Busnel, a director with ACA Group, a provider of risk, compliance and cyber solutions. This type of payment uses tokenization, which replaces your sensitive card data — like the expiration date and card verification value (CVV) — with a unique, random token. If the company you’re buying from doesn’t have your sensitive card information, neither will hackers that hit that merchant with a data breach. Holders of any credit cards, whether you know if they have been compromised or not, are advised to monitor bank statements for any suspicious or unusual activity. These tools scan transactions in real-time, flagging any suspicious charges instantly.
WhatsApp 0-Day Vulnerability Exploited To Hack Mac And IOS Users
More bogus credit card data, personal information, and documents were sold in 2021 compared to 2020, while products, like hacked cryptocurrency accounts and web services such as Uber, are more available. Monitoring your credit is crucial in protecting yourself from credit card fraud on the dark web. By regularly checking your credit reports and statements, you can quickly identify any unauthorized charges or suspicious activity. Look out for unfamiliar transactions or sudden changes in your credit score. If you notice anything unusual, contact your credit card company immediately to report the issue. If you come across any instances of credit card fraud or encounter suspicious activities, it is essential to report them to relevant authorities.
Never Save Your Credit Card Information On Websites
Deep and dark web credit card sites include forums and marketplaces that host the trade and share of illicit content relating to credit cards. For example, Track2NFC allowsyou to convert magnetic stripe data (Track 2). You can use the app tostore the information on your mobile device and make purchases at anyNFC-enabled terminal. Such an app can be used for legitimatepurposes, such as when developers of payment services testNFC-compatible apps, but obviously, cybercriminals use it formalicious purposes. This means you can store information for all your cards in oneconvenient location, making it easy to switch between cards whenpurchasing. Thefact that credit card (CC) information is already stored on thedevice and added to the wallet immediately triggered the attention ofcybercriminals.
MultipleChinese-speaking cybercriminal channels dedicated to carding havebeen identified on Telegram, with some having over 5,946 activemembers. Taking these proactive steps and tapping into available resources can empower you to make informed financial decisions and act swiftly should a data breach occur. In the ever-changing landscape of the digital world, community support can be a powerful ally. Incorporating these simple yet effective habits into your daily routine can make all the difference, keeping you several steps ahead of cybercriminals lurking in the digital depths. Adopting these cybersecurity practices not only protects you from becoming an unwitting participant in dark web transactions but also fosters a greater sense of control over your financial life. BleepingComputer has discussed the authenticity with analysts at D3Lab, who confirmed that the data is real with several Italian banks, so the leaked entries correspond to real cards and cardholders.
Info on the dark web doesn’t show up in your run-of-the-mill search engines. All websites hosting pornography will have to check the age of their users from Friday. This new trend for marketplaces winding down in an orderly fashion is known as “sunsetting” or “voluntary retirement”. A letter posted on its homepage said it had been “a great pleasure to work with most vendors and users”. The darknet is a part of the internet only accessible through special browsing software. Infosec Insider content is written by a trusted community of Threatpost cybersecurity subject matter experts.

Card Data And Markets
Unlike online fraud, this type of theft is harder to detect because the transaction appears as a regular swipe. These details often land there after data breaches, phishing attacks, or malware infections that steal information from unsuspecting users. If your credit card number appears on the dark web, it means someone has likely leaked or stolen it—and now it could be traded, sold, or used without you even knowing about it.
Credit Card BasicsThing To Know About Data Breaches
By taking these simple but effective precautions, you can significantly reduce the risk of your personal information falling into the wrong hands. Protecting your personal information is vital when it comes to guarding against credit card fraud on the Dark Web. Start by regularly updating your passwords for online accounts and using strong, unique combinations that include a mix of letters, numbers, and special characters. To protect yourself, be vigilant while making online transactions, use secure payment methods, and regularly monitor your credit for any suspicious activities. Compromised online accounts can also lead to your credit card information being published on the dark web. A compromised online account is an account that has been accessed without the permission of the person who owns it.
The device reads the data and steals the information from the credit cards swiped at the source. If you notice any unauthorized charges, contact your credit card company immediately. Many newer debit and credit cards come with a feature called “tap to pay.” This feature allows you to conduct transactions without having to insert or slide your card into a card reader. Using your card’s tap-to-pay feature helps keep you safe from credit card skimmers who aim to steal your card’s information.
Once obtained, this information is used for identity theft, fraudulent purchases, and money laundering. Once obtained, these stolen credit cards are quickly sold on the dark web, where they can be used for fraudulent transactions or identity theft. Protecting your credit card information is crucial to avoid financial loss and potential legal troubles. By regularly monitoring your credit, using secure payment methods, and being cautious online, you can minimize the risk of your credit card falling into the wrong hands.

The Price Of Stolen Info: Everything On Sale On The Dark Web
Kim Komando hosts a weekly call-in show where she provides advice about technology gadgets, websites, smartphone apps and internet security. Credit card details with balances up to $5,000 go for $110, and online banking logins with $2,000 or more go for $60. Actual or formally correct ID card numbers are among the most expensive goods on the dark web. Interestingly, a major part of the carding ecosystem revolves around education.
This is why it’s important to review your credit card statement regularly and never ignore anything that looks suspicious, even if it’s for a very small amount. Once a scammer has their hands on your credit card information and is ready to use it, they may start small. The idea is to check if the credit card works first by charging an inexpensive transaction, often for less than $5. Dark Web ID has been an industry leader for years because they never stop innovating to keep businesses out of credential compromise trouble. Arda is a Senior Crypto Threat Analyst at Elliptic with a focus on crypto-based terrorist financing, dark web vendors, NFTs and DeFi-related crime.
- This new trend for marketplaces winding down in an orderly fashion is known as “sunsetting” or “voluntary retirement”.
- Just in the last 3 months millions of unique credit card credentials have circulated across the deep and dark web.
- NordVPN said there is little users can do to protect themselves from this threat apart from not using cards, but added that it is important to be vigilant.
- If you’re connected to a public WiFi network, avoid making any purchases online while you’re connected to the network as this could place your financial data at risk.
- Buyers use these cards to make unauthorized transactions, often attempting to maintain anonymity through the use of cryptocurrencies.
Use multifactor authentication to prevent threat actors from guessing at weak passwords, or getting into your systems with a brute force attack. MFA and strong password requirements will force your employees to use strong passwords and change them often. Once fraud is detected, a business must act immediately by contacting any customers who may have been impacted and contacting the payment processor to report the fraud.