The company operates a strict no-logs policy and protects internet traffic using AES-256-GCM encryption together with a...
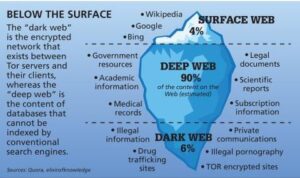
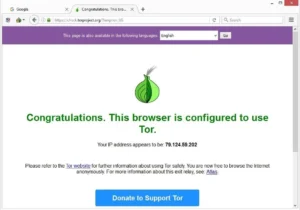
Nowadays, many people use the Tor browser to surf the public internet and navigate the deeper parts...
As always, protect yourself from online threats with mobile Android security or iOS security software. And use...
To send a message or image via ZeroBin, you just need to copy the desired content and...
People often have bad feelings about the dark web, but not everything on it is illegal or...
For example, legitimate sites, such as the BBC, the New York Times, ProPublica, and Facebook, have made their...
Many listings involve stolen personal information, including credit card data, Social Security details, and full identity profiles....
While some reports of dark web murder-to-order are overblown, it is possible to commission acts of cybercrime...
The anonymity provided by the Dark Web makes it an attractive platform for criminals to operate, as...
We conclude by describing several of the effects of the cigarette black market on inmates. Before accessing...